Previously on OPIUM HUM:
Previously on OPIUM HUM:
A study out of Cambridge University has come to the conclusion that there is a sluttiest boy shoe, and baby, it’s the loafer.
“When we look at slutty girl shoes, the range is much broader,” said Lead Researcher Franklin Hoker. “You’ve got stilettos, strappy sandals, those little plastic ones that look kind of bad, but when it comes to the boy shoe, there’s one variety that clearly and definitively rises above the rest: loafers.”
The study found that the general shape and lift of the loafer implies the wearer is down to fuck, but that’s not where the debauchery ends.
“There are so many additional ways to slut up the loafer,” Franklin continued. “You can do two-toned, add a buckle or a platform, and don’t even get me started on the whorey little tassel thing.”
The study found that compared to a control group, men who wear loafers are 50% more likely to have bleached their hair in the last year to 300% more likely to be in a polyamorous open relationship right now.
“Those sluts love to show their little ankles with a bit of sock,” Franklin continued, even though reporters had stopped asking him questions. “They love to clicky clack down the hallway.”
Of loafer wearers, those who opted for a burgundy leather were statistically the sluttiest, followed closely by those who favor a bit of chunk in the heel.
“So, you like to push the boundaries?” Franklin said of burgundy loafer wearers. “We get it, you’re in your hookup era!”
The results of the study sent shockwaves throughout the scientific community, even reaching some of the most powerful leaders around the globe.
“I’d say the loafer is definitely the sluttiest boy shoe,” said French President Emanuel Macron, unprompted.
“We talkin’ slutty boy shoe? Then yeah, we’re talkin’ loafer,” President Biden added. Reporters are unaware when these respective presidents were informed of the study, but the remainder of the G20 Summit at which they made these comments was uneventful.
“At long last, we’ve answered the question at the top of everyone’s mind: how can boys convey that they may be men, but they still want to be a little flirty, a little sexy?” Franklin continued.
At press time, the team behind the study identified that the second-sluttiest boy shoe is the hiking boot, as it implies a gruffness that’s really in right now.
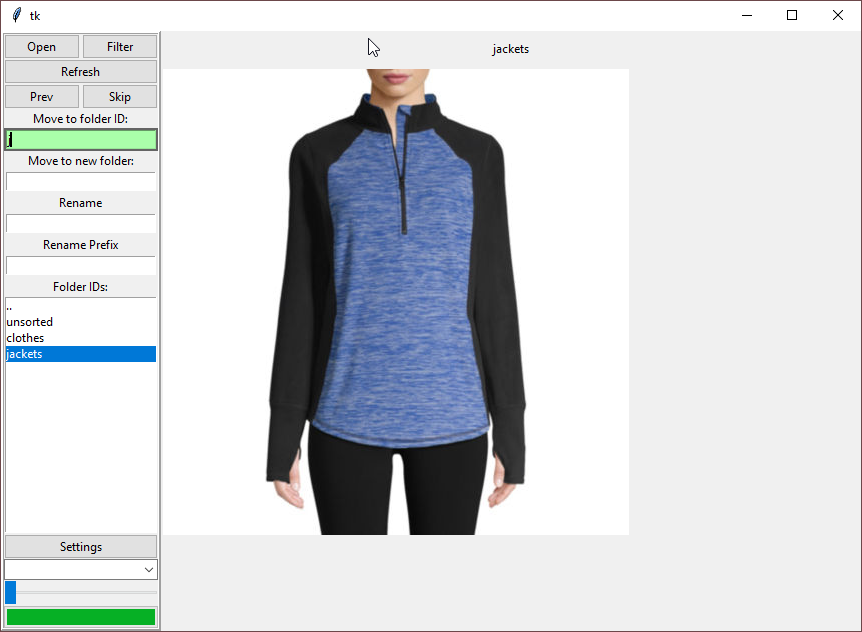
I’ve decided to do a short write-up on a tool I just call “Sorter”. Sorter is something I built for myself to help me organize my own files, and it looks like this:
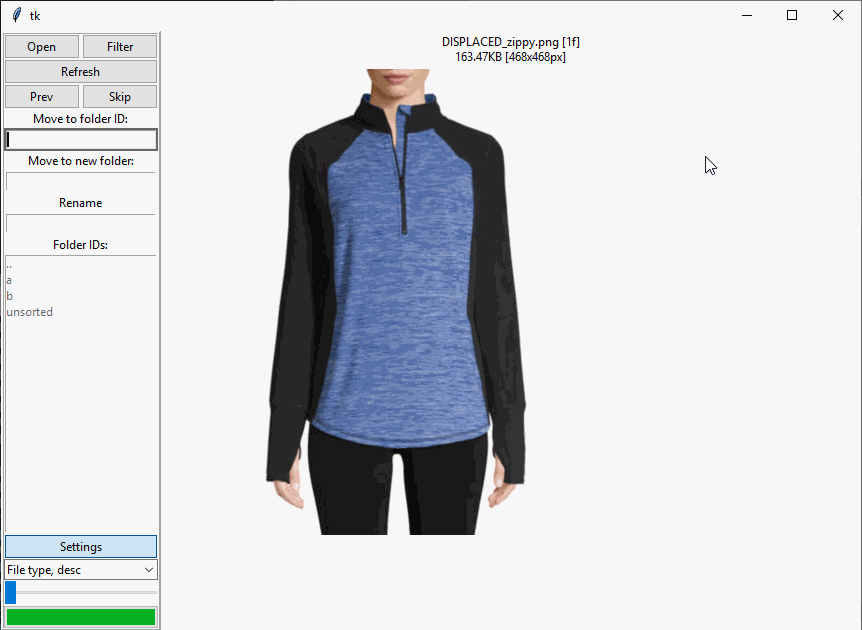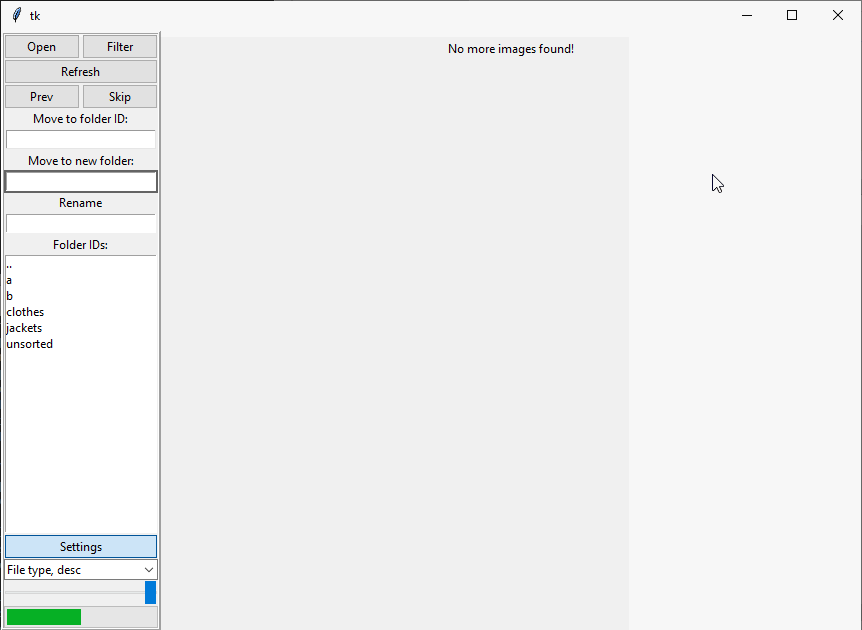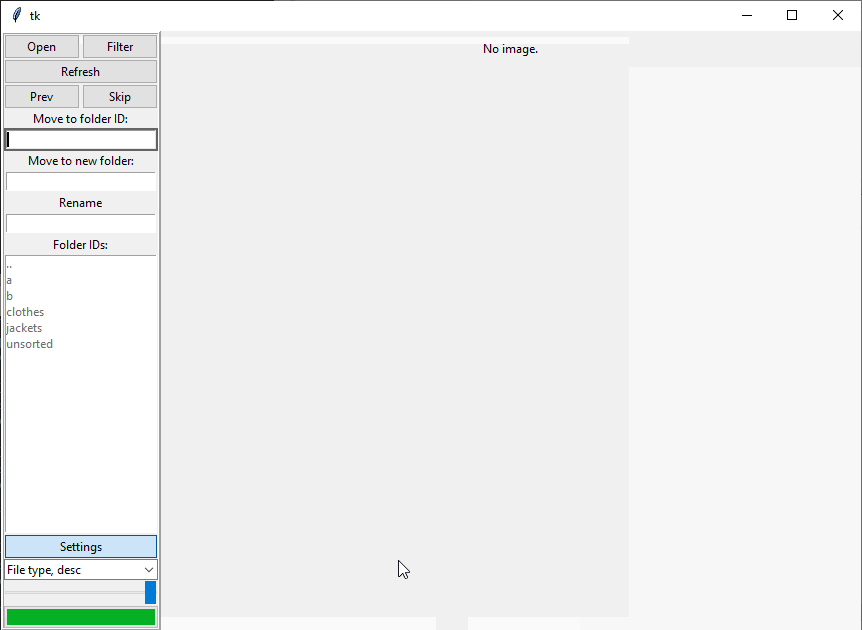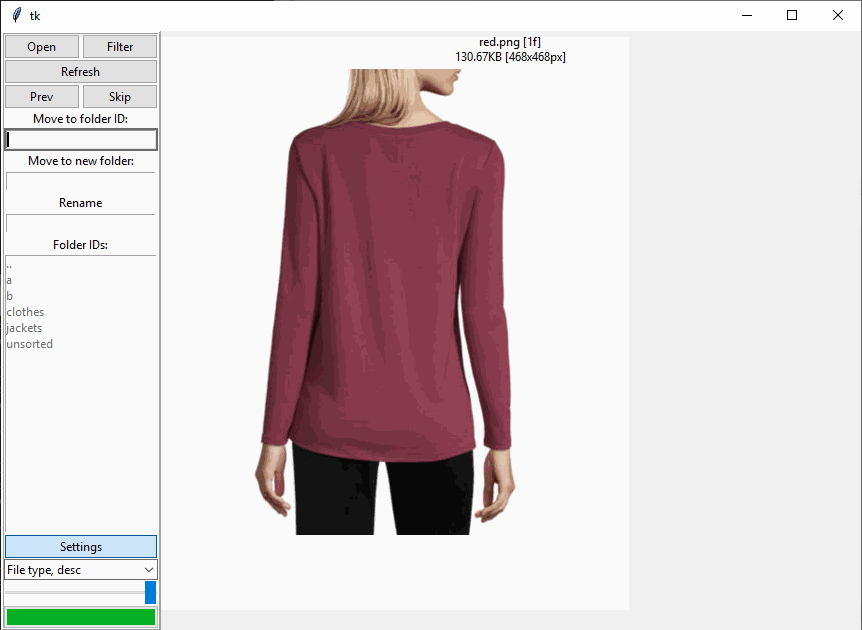
It’s designed to do exactly one thing: move files into subfolders, one file at a time. You look at a file, you decide where it goes, and you move it accordingly. It’s the same behavior you can do with Explorer, but at speed.
You can download it if you want (although it might not be easy to build; check the releases for binaries) but for now I just wanted to talk through some of the features, why I built it the way I did, and the specific features I needed that I couldn’t find in other software.
I made Sorter with pure python and tkinter interface components. Do not make a GUI program with pure pythona and tkinter interface components. It, and its relevant documentation, is ancient and abandoned. From what I’ve seen the modern GUI toolkit to use for a program like this is PyQT, although I haven’t worked with it yet.
Sorter has a “current working directory” you open when you start the program. It expects all “loose” files to be loose in the root of the working directory, or in a folder titled “Unsorted”. Additionally, if there’s an “Unsorted” folder and loose files, it will offer to move them to Unsorted for you.
It creates a list of those loose files and seeks through the list one file at a time. You can filter this list by fileglob; the current default is *.png, *.jpg, *.bmp, *.jpeg, *.tif, *.jfif, *.tga, *.pdn, *.psd, *.gif, *.gifv, *.webm, *.mp4, *.mov, *.webp for images and image-like files.
The “candidate folders” the current file can be moved into are on the list on the left. In the “Move to Folder ID” box, typing a string that matches one of the candidate folders moves the file to that folder.
Crucially, this matching is done aggressively. With only a few subfolders, you usually only need to type one letter to get an unambiguous match.
There are more sophisticated rules that kick in if the first few letters are frequently common. For example, “j e” matches “john ebgert” and not “john arbuckle”. You can even turn on extremely aggressive fuzzy matching that matches freely inside strings, so “u” matches even “qwertyuiop”.
The goal is to make the mechanical operation of moving the folder as fast as possible. For each file, you should be spending as close to 100% of your as possible making decisions about filing, not doing the mechanical act of filing. That’s what computers are for!
Trying to do this with explorer is miserable. The best way I found of doing it is drag-and-drop with two windows open, which means you’ll spend most of your time hunting for the folder in the list and dragging your mouse to the right place. That’s fine for general-purpose use, but it’s no good for bulk sorting.
There are plenty of blazing-fast, efficient tools for moving and manipulating files, but they’re mostly command-line utilities that can’t inspect images. Sorter makes that operation almost instant, and does the moving operation itself in the background, so you can focus on decision making, which is the one thing the computer can’t do.
There are other controls on the left, too. “Move to new folder” ignores the candidate folders and moves the file as-is to a new folder it creates. “Rename” changes the name of the file without moving it, and “Rename Prefix” adds the prefix you specify to the filename. (This is good for adding indexes or page numbers or anything you want to easily sort on!)
Sorter mainly focused around quickly inspecting images, but there are also some fallbacks for other formats, like grabbing the first frame of a video, or getting a list of a zip file’s contents, or just reading the windows metainfo of the file.
alright, it's time to embark on a new mission, over the course of the next few blog posts/weeks/months we are going to try and slowly ruin the stalkerware industry. some of the most vile, somehow not illegal, types of businesses to exist. but to do this i should first do a basic intro into what stalkerware is and why it's so bad.
what is stalkerware
stalkerware is an umbrella term for most privately, commerically available spyware, more specifically ones hidden from the target (spyware that doesnt hide its purpose (such as child monitoring software like life360) will be referred to as watchware in this series). it is also often referred to as spouseware due to the prevalence in use by controlling partners to "catch cheating partners", but i dislike this term because use of such software against children (or by employers against employees) is just as bad and abusive as against partners.
stalkerware usually works by giving the spying person access to a dashboard where they can track all phone activity of a victim, be it phone calls, text messages, notifications, geolocation, their photos or anythign else you can imagine, as well as a mobile (or desktop) applcication. the client malware component usually either requires for the spying person to either have physical access to a device to install a client which hides itself upon finished setup, or sending their victim a link to a disguised application (such as a ringtone creator application) which then asks for an activation code also provided by the spy.
a lot of the industry advertises in a way that implies that software such as this is to be used to "keep children safe", but some just blatantly say you can use it to secretly spy on your partners. but absolutely without exception basically all companies in this industry tell you that you need consent to use tools such as these (i am curious now has anyone ever been convicted anywhere for secretly spying on their partner/children?).
why is it bad
ok i feel like it should already just be clear from the previous section why stalkerware (and watchware) is bad. generally even with consent. but just to make my points more explicit and point out some extra reasons for why it's bad, here we go.
- using, especially hidden, tracking tools on anyone is controlling abusive behaviour
- everyone has a right to privacy
- yes that includes children (children are not your property)
- even with ""consent""/informing the person to be spied on, especially if they are your child or you otherwise are someone with authority over them, it is still controlling. children deserve privacy and their own spaces, if they trust you they will talk to you about shit thats going on, if they dont youre only going to ruin everything more by fucking spying on them.
- stalkerware providers almost always end up getting hacked, leaking all the detailed recorded data of everyone.
so what is this series gonna be about
alright so, see point 5 above? yea that, i will be collecting stalkerware breaches sent to me, looking into companies myself, and blogging about them one by one. revealing (as far as possible) how unsecure they are, who's behind them, trying to get comment, and helping other journalists with stalkerware related reporting. two blog posts are already in the works, and if you have anything to contribute to potential reporting (vulns you find in stalkerware software, leaked data, investigations, insider info [your identity will be protected], etc) or are a journalist looking to cover anything in this series in more detail, contact me.
note: the EFF has also been doing really important work rooting out stalkerware for many years now (cool website to learn even more about stalkerware too), which i have previously contributed to with other work, which i will not link due to it being linked to my deadname
Paper: Building and revising adaptive capacity sharing for technical incident response
Since last week I was at a conference where John Allspaw presented content from this paper, this week I decided to go and take a look in my notes for Richard Cook and Beth Adele Long's Building and revising adaptive capacity sharing for technical incident response: A case of resilience engineering, and put them in here.
This paper was published in the journal of Applied Ergonomics and represents a recent and significant milestone for Resilience Engineering. In short, a lot of Resilience Engineering as a discipline is far closer to Resilience Studying, in that people look at what resilience is like after it has been noticed in the wild. This paper is one of the first peer reviewed ones that explicitly looks at it from the point of view of Engineering, meaning that you find ways to create conditions that are likely to promote resilience emerging.
It's a case report by looking at what was being done at a tech company and starts with a brief description of the industry: high-stakes work, high technical skill, countless anomalies, rapid growth, increased demands and complexity, etc. There's a quick reference to Woods' categories of resilience, and a reminder that we're dealing with categories 3 and 4 here:

What they noticed at a given org was the existence of a specialized multidisciplinary team dealing with bigger thornier incidents:
Within the company, normal work is done by small teams. Teams maintain an on-call rotation and are responsible for handling events that affect their assigned components. While this approach produces efficient response to many anomalies the event salvo contained events that were difficult to troubleshoot. In response, a group established a support cadre to assist in response to high severity or difficult to resolve events. This group would provide a deep technical resource that could be called on to support incident response.
The support group was composed of eight engineers and engineer managers from the different technical units. The group organized an on-call rotation to provide a reserve of engineering and operational expertise. One member of that group would participate in incident response when specific thresholds (e.g. consequences for customers, incident duration) were reached. This approach was taken without altering the workload of the support group members’ teams.
That support group had weekly meetings to review and adjust their approach. They noted a few good properties: incidents closing faster, no "fire alarms" that distracts everyone, etc. They also found out cases like "there's been an incident lasting for long" and wrote tools to automatically ping the support team so escalation didn't rely on small team members realizing they are getting bogged down.
At some point though, the demand became a burden on members of the group and some left, so the company was forced to figure out how to create a pipeline to make it sustainable. Since the org saw the importance, they increased the status, added financial incentives, excluded members from their own team's rotation, etc.
Key characteristics of an Incident
The authors point out 3 key characteristics of an incident:
- Tempo: how often incident happens. This org had a dozen a week. Too low and you can't accumulate experience, and too high and you would exhaust everyone, create weird expertise concentration, etc.
- Duration: incidents need to be long enough for sharing to take place but not be so long that they damage the "donor" team
- Magnitude: if all incidents are minor, there's no benefit in sharing resources. If all incidents are major then highly expert-centric units would make sense. Having a variation in magnitude makes the sharing of employees and knowledge workable.
They point out that:
The situations where sharing capacity is useful must also be familiar enough to the group members that each is able to “get up to speed” quickly enough to make that individual’s contribution useful.
If everyone only has general knowledge, sharing won't work as well as if people are routinely dealing with the specifics of local conditions.
They point out that by the nature of incidents, the support group needs to be interruptible and available for mobilization. If their worklads are hard to interrupt (think surgeon in an operating room) then they'd not be available to share their knowledge in an incident. Easy communications are also key, particularly in globally distributed businesses, where tools support instantly reaching out to lots of people. The authors theorize that "resilience itself is highly dependent on communications."
Sustaining
What's interesting here is that setting up the initial team wouldn't work long term:
In this example it quickly became apparent that simply sharing existing adaptive capacity would consume it and that sustaining the ability to share adaptive capacity requires resources and attention. The individuals and their expertise need to be replenished. Indeed the cadre of experts from which the group was drawn is itself continually changing. Given the rapid pace of change in this domain what constitutes useful expertise will continue to evolve. Whether the approach is durable is very much an open question.
These features suggest that successful resilience engineering may – at least at present – depend on identifying and exploiting situations and resources that are already well configured.
They then provide table 3, which is probably the perfect TL:DR; to the article:

Woods’ theory of graceful extensibility predicts that resilience will appear as individual “units of adaptive behavior” exhaust their own adaptive capacity and obtain additional capacity from other units in their network. This means that it's not about being able to sustain all challenges for each individual unit (person or team or whatever), but about being able to recognize you're going out of capacity, and then getting help and readjusting how tasks are accomplished.
The unit here is a team of people that, from time to time, is required to cope with an incident. When an incident threatens to exhaust that group’s capacity it can obtain support from those in surrounding units.
They provide this little image, where 'UAB' stands for "Unit of Adaptive Behavior" and sort of graphically puts the 'support' from a neighbouring unit:

This image is purposefully drawn to look general like that, because it could apply as well to teams pushing on the operational boundaries as it would to Osteocytes communicating to control bone remodelling.
They conclude:
Graceful extension of the group’s capacity to respond is an expression of resilience. What makes the example a case of resilience engineering is the deliberate, iterative, and empirically based creation and modification of a method to make that makes the expression of resilience–the sharing of adaptive capacity–efficient, effective, and–most of all–sustainable.
The resilience engineering described in the example is the deliberate adjustment of adaptive capacity sharing. The organization engineered a way for sharing to take place. This was originally driven by an economic concern – the need to keep the operational cost of managing incidents in check. Over time, the engineering has refined the sharing to make it better and more efficient. The engineering also set up the conditions needed to replace and grow the adaptive capacity.
They state that given the right conditions, resilience engineering is already taking place in these organizations and could orient more practical studies of these approaches. It also hints at ways contexts could be shaped to either enhance or protect these properties.
I know it's one of the things we do at work sometimes, where we don't try to remove all incidents—they're part of a healthy tempo—and a period of calm with nothing is something I interpret as a signal to do simulations and chaos engineering.

